VPN Tunneling Protocols: What They Are and How They Work
Understanding What VPN Tunneling Protocols Are
The online world has taken over every aspect of our lives, transforming and multiplying our opportunities as we and technology evolve. Not only has the adoption and adaptation of technology changed the way we work and play today. But it has also altered vital parts of our lives, taking them from traditional analogue methods to superfast digital actions.
The speed at which technology is moving and taking us has also created gaps that are often overlooked. Online privacy and protection have been one of the biggest concerns of the online world. With so much data and information available at our fingertips and mass amounts of personal data online, cybercrime has created opportunities that have peeked in the global pandemic.
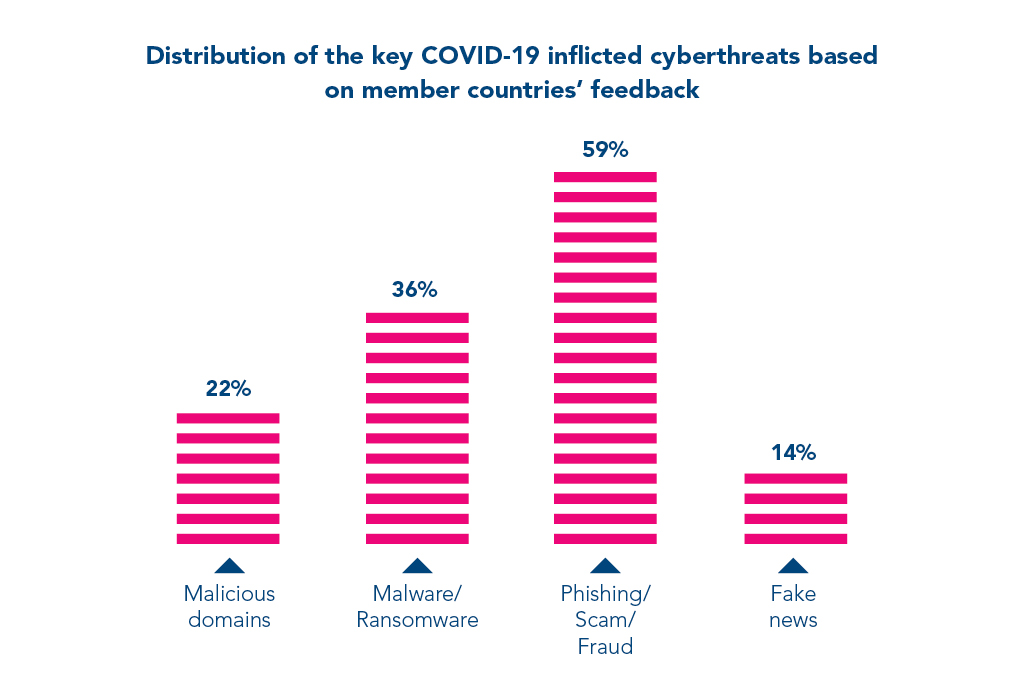
(Image Source: Interpol)
For this reason, many use VPNs to keep their connection secure. Connecting through a VPN creates an established connection between hardware devices such as laptops and computers to the internet. All the data and traffic from the device runs through an encrypted virtual tunnel which disguises the IP address making vital information like location unavailable. This helps to make the connection secure and exempt from any external attacks that might occur.
How VPN tunnelling works
In order to securely connect a network internet connection, users need to sign up to a VPN service provider which helps to hide their IP address. Before visiting desired websites, users will need to log into their VPN, which will also hide their data from their internet service provider (ISP). This means when users click on downloadable content, the ISP will not be able to see whose activity it is as the VPN IP address will show instead. This is how the data transfers securely through a VPN tunnel which masks all activity.
However, simply masking the data is not enough. So many VPN service providers encrypt the data that is sent and received online, scrambling it into illegible information, making it virtually impossible for online criminals to understand, even if they get their hands on it.
Introducing the blanket of protection to any online activities a user may do creates an unbreakable barrier for government bodies, hackers, and cybercriminals to see any online activity through the VPN. Most VPN service providers have protocols that all have different protection levels, which is where VPN tunnel protocols come into play.
VPN tunnel protocols
As there is a range of VPN service providers, naturally, they are not all equally effective at protecting online privacy. This means that the strength of the tunnel that protects user data is typically based on the type of tunnelling protocol the service provider issues.
In some cases, the protocols are outdated, which means they may not provide the correct levels of data encryption required to deter hackers and snoops online. With this in mind, it is generally a good idea to work with VPN providers who offer the most robust and most effective tunnelling as possible. Here is a look at some of the different types of protocols available.
Open VPN
An Open VPN is one of the strongest protocols available online by VPN service providers and works with many major operating systems commonly used daily, such as Android and iOS systems. It is considered the top form of VPN tunnelling protocol because its encryption capabilities are especially strong, and it is adept at getting past firewalls.
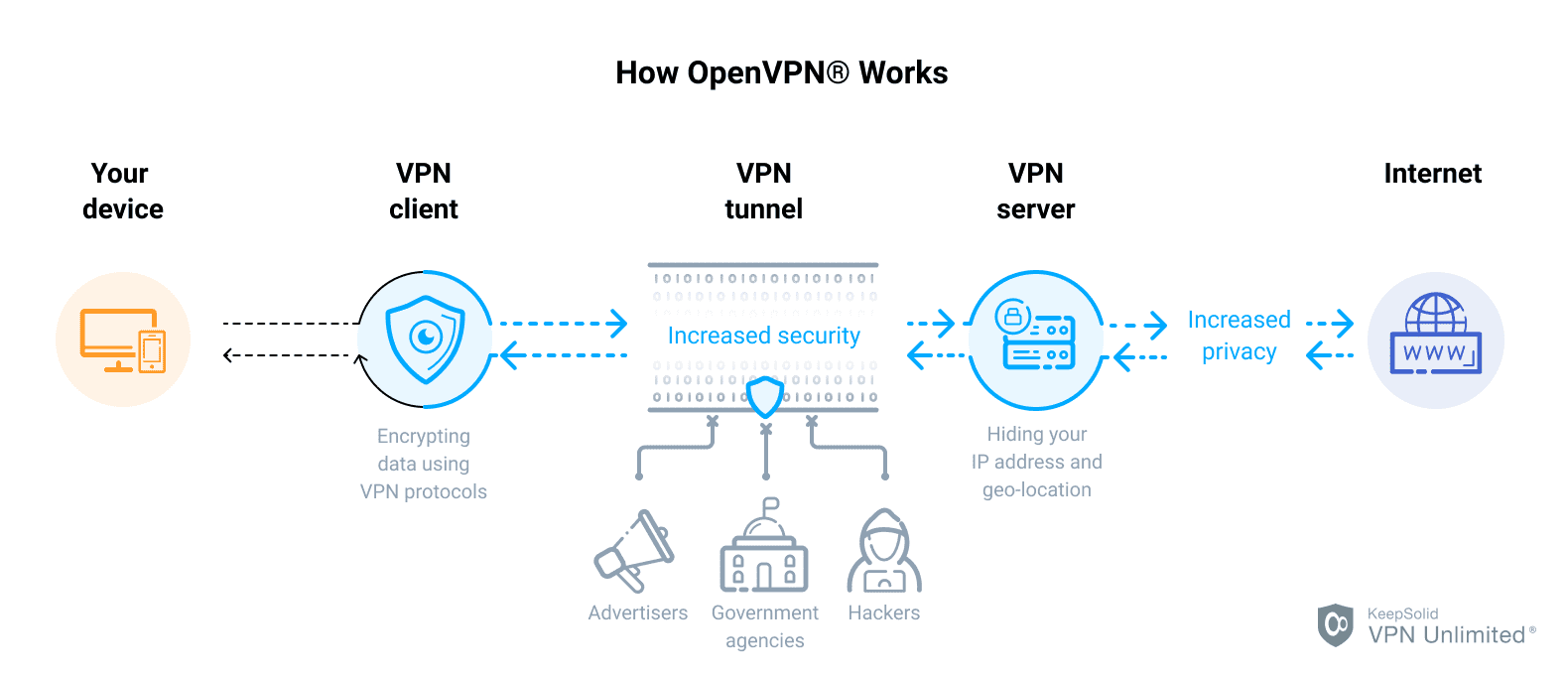
(Image Source: VPN Unlimited)
The open VPN source code is continually and regularly vetted by a security community that are able to pick up potential security flaws, making it one of the best protocols around. However, it uses AES 256-bit encryption to help protect data packets and can be hard to configure. Still, once set up, it hosts a wide range of cryptographic algorithms which effectively and securely keeps internet data secure and, as mentioned, bypasses firewalls with speed and secure connection.
PPTP
One of the oldest protocols that is still currently being used is the Point to Point tunnelling protocol. It was originally developed by tech giant Microsoft and was released on one of their most favourable systems, Windows 95. The way PPTP works is by simply encrypting user data into small packets of information that are then sent through a tunnel created over the user’s network connection, making it secure.
Due to its low encryption levels, it is one of the most straightforward protocols to configure. But with this in mind, its fast speed does come at a cost as its level of encryption is weak considering the standards available and needed today. For this reason, it is easier for a hacker to gain access and crack the encrypted data.
SSTP
Making security easy for Windows users, Secure Socket Tunneling Protocol (SSTP) has the ability to transport data through the secure sockets layer (SSL). For this reason, the SSL makes internet data going through the SSTP very secure. In addition, SSL can also be used in conjunction with Transport Layer Security.
Adding this to a web browser provides an added layer and secure connection to the device being used to browse the internet. It is generally a safe option to go with as it does not use fixed ports, making it easier to get through firewalls. However, the downside of using it is its inability to be flexible with other operating systems, shutting down its own potential.
L2TP/IPSec
Layer 2 Tunneling Protocol (L2TP) is typically used in conjunction with Internet Protocol Security (IPSec) and generally creates a more secure protocol than PPTP. The way it works is L2TP encapsulates the data, but the data is not adequately encrypted at this stage. This is until IPSec wraps that data in another layer, wrapping it in two layers of encryption. This helps to secure the confidentiality of the data packets as they travel and make their way through the tunnel.
It provides an AES-256 bit level of encryption which is one of the most advanced encryption standards that can be put in place, but due to this, it does work slower when compared to PPTP, and it does have issues when attempting to bypass restrictive firewalls due to its fixed ports. However, it’s still a very popular protocol, thanks to the high level of security it is able to offer.