Types of VPNs and Protocols
Let's explore different types of VPNs and Protocols
Virtual private networks help users to connect to a private network on the internet to generate greater levels of security and freedom for their browsing. VPNs establish encrypted connections known as VPN tunnels, and these help to make all data passing through entirely private and safe from prying eyes.
VPNs work with various different protocols that are dependent on various network layers. But what different types of VPN are there? And how do their different protocols work? Let’s take a deeper look into the rich and varied world of internet privacy, and the integral role that VPNs play in delivering safety online:
The Different Types of VPN
Essentially, there are two different forms of virtual private network. Both do distinctly different jobs, so it’s certainly worth understanding the variations between them:
Remote Access VPN
Remote Access VPNs help users to connect to a private network and access all of its services and resources from a remote location. The connection between the user and their private network takes place through the internet and the location is fully secure.
This type of VPN is particularly useful for employees who work remotely for their companies either from home or whilst on location, or individuals who are looking to browse the web securely in their leisure time.
In the case of an employee of a company, while they’re out of the office, they can utilise a VPN to connect to their business’ private network in order to remotely access files and resources on the network.
Outside of work, private users of VPNs typically use the service to bypass regional restrictions on the internet to access websites that would otherwise be blocked. This can be particularly popular for users wishing to access overseas video streaming services that wouldn’t be available locally.
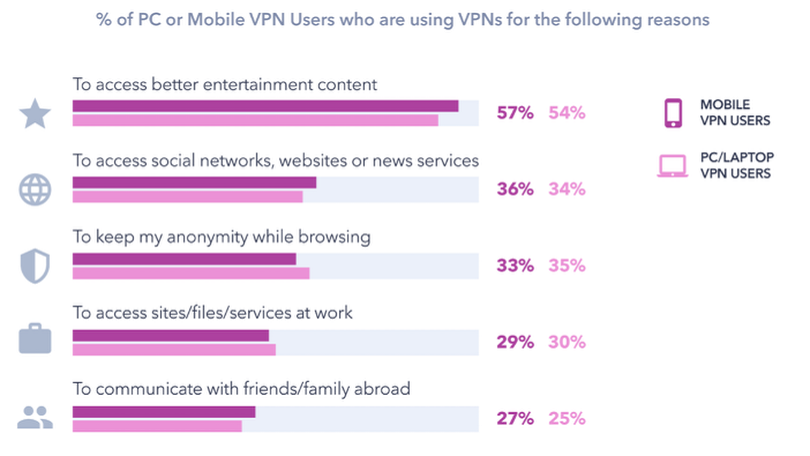
(Image: PCMag)
As the table above shows, the majority of VPN users for both smartphones and desktops alike prefer to use the service to access better entertainment content – with other factors like browsing content and anonymity also ranking highly.
Site to Site VPNs
On the other hand, site-to-site VPNs, also known as router to router VPNs, are commonly used in large companies, or organisations, with multiple branch offices in various locations. These companies use site-to-site VPNs as a means of connecting to the network of one office location to another location.
This can make the sharing of sensitive information and company-wide protocols far easier and frictionless, no matter the distance between locations.
What are VPN Protocols?
Now we have an understanding of the two key forms that VPNs can take, what about their respective protocols?
VPN protocols determine how data is routed through a connection. These protocols have many different specifications based around the benefits and desired circumstances that surround them. For instance, some VPN protocols look to prioritise data with speed whilst others are more intent on masking or encrypting data packets for the sake of better security.
Let’s look at the five most common protocols that can be found alongside the VPN ecosystem:
1. PPTP
PPTP, or a Point-to-Point Tunneling Protocol is one of the oldest VPN protocols active today. Created in the 1990s by Microsoft, PPTP arrived alongside Windows 95 and was designed to accommodate dial-up connections.
As technology developed, the basic encryption of PPTP was cracked by hackers, which compromised its level of protection. However, because of its more simplistic level of encryption, PPTP is capable of delivering the best connection speeds for users who are more interested in a quick service rather than a bulletproof level of security.
It also boasts a wider level of support due to its longevity, making it a potentially strong choice for people wishing to tap into geo-locked content or video games without ISP-imposed restrictions.
2. IPSec
Internet protocol security (IPSec) is a procedure for keeping records safe from a complete gateway of network and host-to-host communication. It creates a means of protecting the IP network of end-to-end users. IPSec helps to enhance the security of users by providing the public or private keys necessary to lock and unlock data – making encryption and decryption modes much more accessible.
IPSec develops an authentication scheme to help appropriately check on individual connections. It also makes sure that any data being sent and received is required to pass the encryption step – meaning that this protocol can split into two modes: either transfer mode or tunnel mode, with tunnelled connections encrypting data and hiding its passage accordingly.
3. L2TP
Layer 2 Tunneling Protocol is often combined with IPSec to set up an extra-secure virtual private network connection. Layer 2 tunnelling helps to create a secure passage between 2 L2TP connection focuses whilst the IPSec protocol swings into action by encrypting data and keeping a more secure correspondence between the tunnel intact.
4. OpenVPN
On the flipside to PPTP protocols, OpenVPN stands as an open-source protocol that enables developers to access its internal coding. This has aided OpenVPN to grow in popularity due to its ultra-secure AES-256 bit key encryption coupled with 2048-bit RSA authentication and a 160-bit SHA1 hash algorithm.
Essentially, the complexity of OpenVPNs encryption makes this open-source solution one of the strongest on this list, but greater security generally comes at the cost of slower connection speeds. This means that if you’re looking to handle confidential data, OpenVPN may be the solution for you, but if you’re looking to watch a region-locked movie, you may find better solutions elsewhere.
5. TLS and SSL
Transport layer security (TLS) and secure sockets layer (SSL) encryptions create a VPN connection where your internet browser conducts itself as the user, and client access is precluded to explicit applications only – rather than through the whole network. Online shopping, for instance, usually utilises TLS and SSL protocols as a means of keeping the details of customers safe as they make purchases.
Furthermore, it’s not too tricky to change the SSL layer by internet browsers and with practically no activity needed from the client as internet browsers come incorporated with TLS and SSL – meaning that you’ll already have a layer of VPN-based security even without finding the help of a dedicated service.
You can find which websites already run secure sockets layer connections by checking to see whether they feature ‘HTTPS’ in the underlying of their URL, rather than HTTP.
The technology surrounding virtual private networks is constantly evolving in order to combat the threats of users with bad intentions. But in knowing what the various types of VPNs are and the different protocols that are used to support them, you can act decisively in finding a virtual private network solution that suits your needs. Whether you’re looking for speed or security, there’s always a VPN out there that can match your ambitions.